Users
The Users page allows you to:
- create and edit users
- assign roles and access zones
- manage login credentials (multiple per user)
- manage the user’s Two-Factor Authentication (2FA)
Quick start
- Click Add to create a new user
- Enter the user’s basic information
- Assign Role and Zones
- Configure the Credentials (login method)
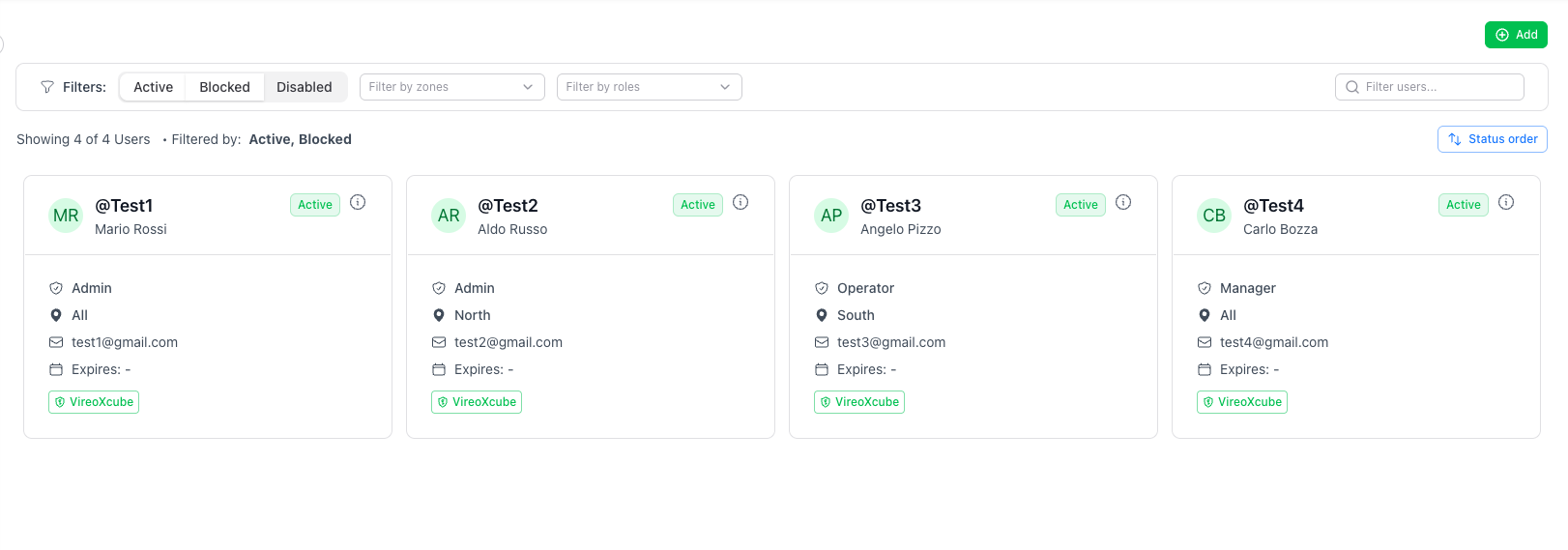
Users list
Users are displayed as cards. Each card shows the main information:
- Username
- First and Last name
- Status (e.g. Active, Disabled, Blocked): indicates whether the user can access the system.
- Active: the user is enabled and can log in.
- Disabled: the user is disabled and cannot log in.
- Blocked: the user is blocked for security reasons or by an administrator’s decision.
This status is used to temporarily prevent access, for example after suspicious activity or an administrative action.
Currently, the Blocked status is applied only through administrative actions.
- Assigned Role
- Enabled Zones
- Account expiration date (Expires), if configured
- Associated Identity provider (e.g. VireoXcube)
Clicking on a user card opens the user details, where (if authorized) you can edit profile and security settings.
Search and filters
At the top of the page you can quickly find users and narrow down the list:
- Search: Filter users…
- Status filters: Active, Blocked, Disabled
- Zone filter: Filter by zones
- Role filter: Filter by roles
- Status or alphabetical order: Status order button. By severity: Blocked, Active, Disabled
Create a new user
User creation is a guided process in 3 steps.
Step 1 of 3 — User Information
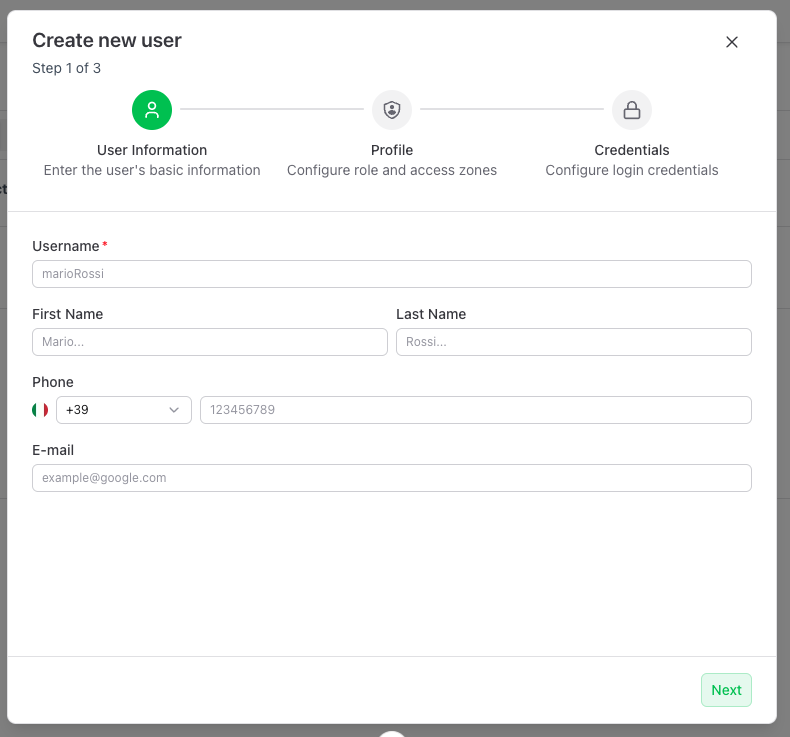
Enter the basic data:
- Username (required)
- First name
- Last name
- Phone
Click Next to continue.
Step 2 of 3 — Profile

Configure permissions and access scope:
- Role (required)
- Zones (required)
Click Next to continue.
Step 3 of 3 — Credentials

Configure the login credentials (required):
- Name Credentials (e.g. Default)
- Name Provider (Identity Provider, e.g. VireoXcube)
- Additional fields depending on the provider, for example for an Internal Identity Provider:
- Password
- Repeat Password
Click Add to complete the creation.
User details
Opening a user shows a set of tabs.
Tab: Profile
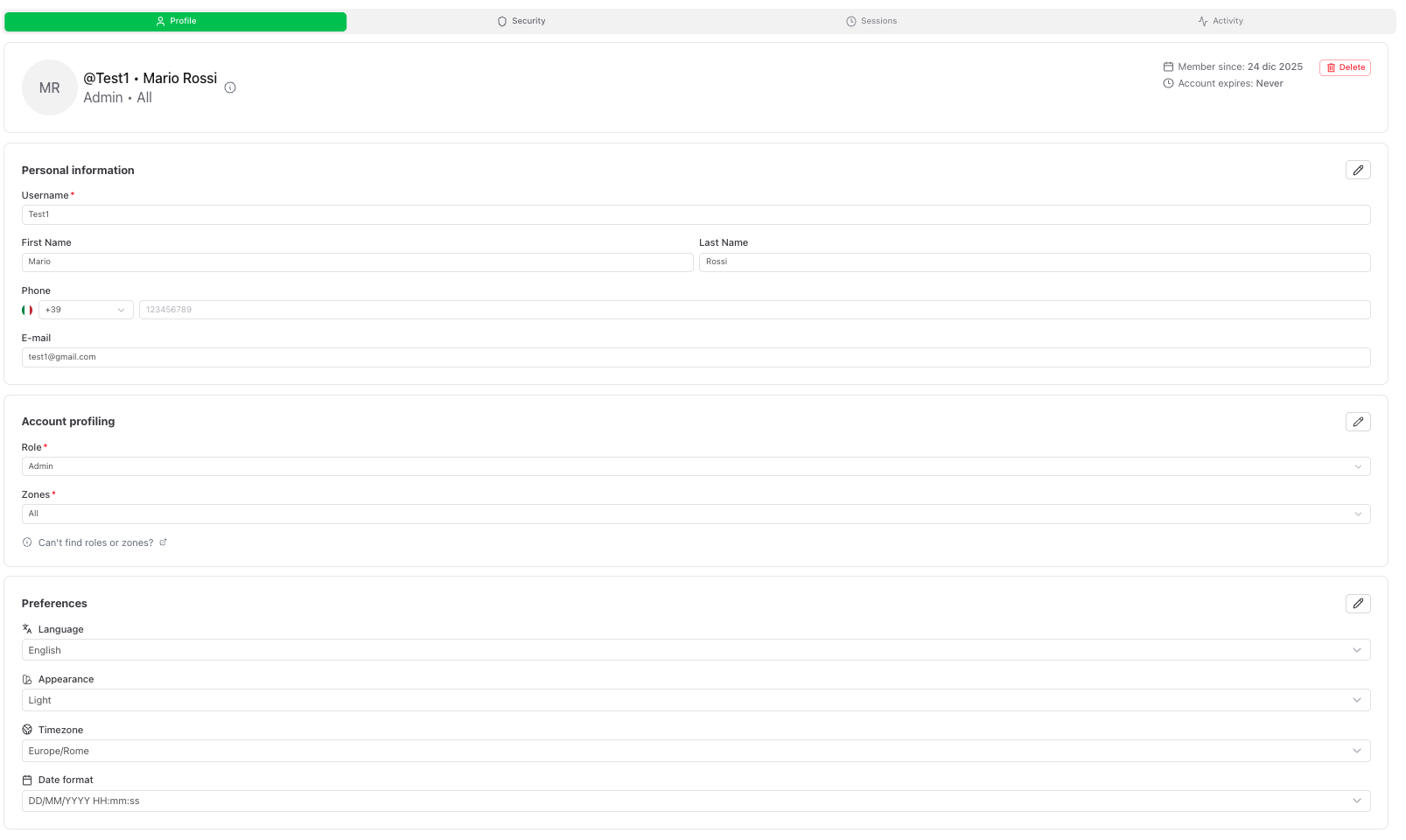
Contains:
- Personal information (Username, First name, Last name, Phone, Email)
- Account profiling (Role and Zones)
- Preferences (Language, Appearance, Timezone, Date format)
To edit a block of information, use the edit (pencil) icon in that section.
Available action:
- Delete: permanently deletes the user (irreversible)
If a user has already performed operations in the system (such as commands, alarm acknowledgements, or other actions), the system must keep the related logs.
In these cases, instead of being permanently deleted, the user is automatically disabled, preventing access while preserving the activity history.
Security and credentials
Tab: Security
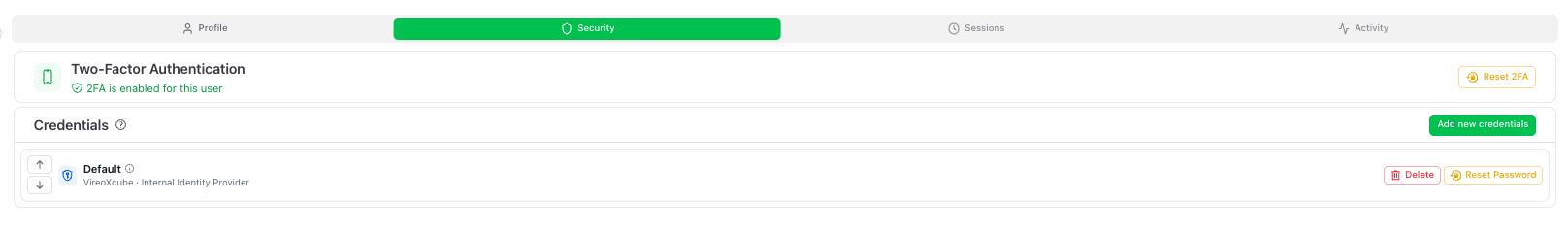
This tab includes:
- Two-Factor Authentication (2FA) status
- the list of configured Credentials
- management actions (reset, add, delete)
Two-Factor Authentication (2FA)
2FA is user-wide (not per credential).
If a user has multiple credentials, they all share the same 2FA.
Available action:
- Reset 2FA: resets the user’s 2FA
After a 2FA reset:
- the user must set up 2FA again at the next login
- the QR code will be shown again during the setup process
Credentials (login methods)
A user can have one or more credentials. Each credential is linked to an Identity Provider.
Typical actions on a credential:
- Reset Password: resets the password for that credential
- Delete: removes the credential
Reset 2FA affects the user, regardless of which credential is used to log in.
Credential priority
When a user has multiple credentials, they are ordered by priority. The credential with the lowest priority number appears first in the list.
When you add a new credential, it is automatically assigned a priority lower than all existing credentials (making it the first in the list).
Add new credentials
Use Add new credentials to add another login method for the same user.
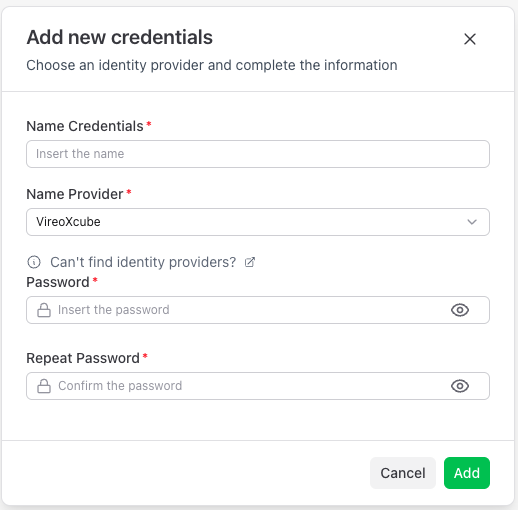
Required fields:
- Name Credentials
- Name Provider
- Password
- Repeat Password
Use this when:
- you want to allow login through a different provider
- you want to add additional credentials for the same user
Account expiration
Users can have an optional expiration date set on their account. When an account expires:
- The user can no longer log in to the system
- The account is automatically treated as disabled
To set an expiration date:
- Open the user's profile
- Edit the account section
- Set the Expires date
User status
Users can have one of the following statuses:
| Status | Description |
|---|---|
| Active | User is enabled and can log in |
| Disabled | User is disabled and cannot log in |
| Blocked | User is blocked for security reasons or by administrator decision |
Frequently asked questions
Can a user have multiple credentials?
Yes. A single user can have multiple credentials, each linked to an Identity Provider.
Does 2FA apply to all credentials?
Yes. 2FA is shared across all of the user's credentials.
What is the difference between "Reset Password" and "Reset 2FA"?
- Reset Password changes the password of the selected credential
- Reset 2FA resets the user's 2FA (they must set it up again at the next login)
Why do I see nothing in "Sessions" or "Activity"?
Because those tabs are not implemented yet.
What happens when a user account expires?
When the expiration date is reached, the user can no longer log in. The account is treated as disabled but can be reactivated by an administrator by extending or removing the expiration date.
What is the credential priority for?
The priority determines the display order of credentials in the Security tab. It does not affect which credential the user uses to log in.
